In the ever-evolving world of cybersecurity, businesses face a relentless stream of threats. From ransomware and phishing attacks to insider abuse and supply-chain compromises, the risks are multiplying in both scale and sophistication. Yet, amid this chaos, one question constantly arises: how should organizations structure their detection and response capabilities?
Two prominent answers have emerged over the last decade — SIEM (Security Information and Event Management)and MDR (Managed Detection and Response). These solutions are often mentioned together, sometimes even interchangeably, but they serve very different purposes. Understanding their distinctions — and how they can complement each other — is vital for designing a modern, resilient security posture.
1. The Foundation: What Is SIEM?
A SIEM, at its core, is a technology platform designed to collect and analyze log and event data from across your IT environment. Think of it as a massive security brain that centralizes information from firewalls, servers, endpoints, identity systems, and cloud services — transforming endless streams of raw data into meaningful insights.
How It Works
SIEMs act as a central nervous system for security operations:
- Collection: Logs from network devices, applications, and cloud services are ingested into the SIEM.
- Normalization: Data from different sources is standardized so it can be correlated and compared.
- Correlation: The SIEM applies rules and analytics to detect patterns — for example, a series of failed logins followed by a privileged access request.
- Alerting and Reporting: When suspicious activity is detected, alerts are generated for analysts. Dashboards and reports help with ongoing monitoring and compliance.
The Power of Visibility
SIEM provides visibility across the enterprise. With hundreds of systems producing data, visibility becomes the foundation for both detection and forensic analysis. It allows teams to investigate incidents, understand what happened, and ensure compliance with regulations like PCI-DSS, HIPAA, or ISO 27001.
The Catch
However, SIEMs don’t magically stop cyberattacks. They inform; they do not act. Organizations still need skilled analysts to interpret alerts, fine-tune detection rules, and respond. Without this human element, SIEMs can easily become expensive log warehouses producing endless false positives.
2. The Evolution: What Is MDR?
If SIEM is the “brain,” MDR (Managed Detection and Response) is the nervous system and reflexes combined — it detects threats and helps you respond immediately. MDR emerged as organizations realized that owning tools alone wasn’t enough. They needed constant vigilance and expert intervention, 24/7.
What MDR Does
MDR is a managed service that combines technology, threat intelligence, and human expertise to:
- Monitor: Continuously observe systems, endpoints, and networks for suspicious activity.
- Detect: Use advanced analytics, behavioral models, and threat intelligence to identify true threats.
- Investigate: Expert analysts validate alerts and determine severity, scope, and impact.
- Respond: Contain or guide the containment of active threats — often isolating endpoints, blocking malicious IPs, or coordinating remediation steps.
Human Intelligence + Automation
Unlike SIEM, MDR doesn’t just collect data; it acts on it. An MDR provider maintains a Security Operations Center (SOC) staffed by analysts and threat hunters who work around the clock. They not only react to alerts but also perform proactive threat hunting — searching for signs of compromise that may not have triggered automated rules.
For Whom It’s Ideal
MDR is perfect for organizations that lack the time, staff, or expertise to build an in-house 24/7 SOC. Instead of buying and managing multiple security tools, they subscribe to a service that delivers outcomes: faster detection and reduced response times.
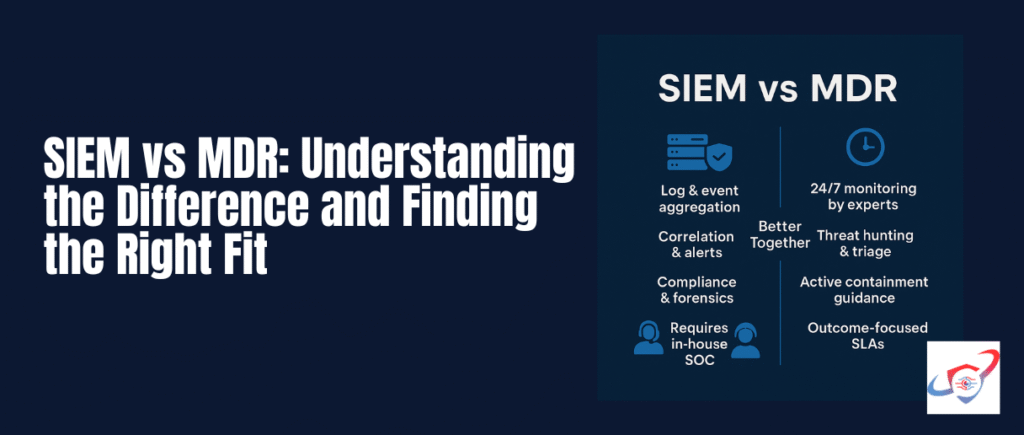
3. The Key Differences: SIEM vs MDR
At a glance, SIEM and MDR seem to overlap. Both deal with detecting and responding to threats. But the who, how, and what are fundamentally different.
Here’s a clearer breakdown:
| Category | SIEM | MDR |
| Type | Technology platform | Managed service |
| Core Function | Collect, correlate, and analyze logs | Detect, investigate, and respond to threats |
| Who Operates It | In-house security analysts | External security experts (SOC team) |
| Response Capability | Generates alerts; requires manual follow-up | Provides hands-on or guided response actions |
| Cost Structure | Licensing, storage, and maintenance costs | Subscription-based service, often per-endpoint |
| Time to Value | Longer setup and tuning period | Faster — provider handles operations |
| Best For | Mature organizations with established security teams | Organizations needing 24/7 monitoring and expert response |
The Core Distinction: Ownership
- SIEM gives you the tools and data to detect threats.
- MDR gives you the people and expertise to detect and respond to them.
The distinction is similar to owning a medical lab (SIEM) versus hiring a doctor (MDR). The lab provides data, but you still need someone to interpret and act on the results.
4. The Strengths of SIEM
Despite the rise of managed services, SIEM remains a cornerstone of enterprise security for several reasons.
4.1. Comprehensive Visibility
A SIEM integrates logs from virtually any device, giving unparalleled insight into network and system activity. It’s the central command center for your security telemetry.
4.2. Compliance and Audit Readiness
Many industries mandate log retention, audit trails, and incident tracking. SIEM platforms make compliance reporting almost automatic.
4.3. Long-Term Forensic Analysis
Because SIEMs store massive amounts of historical data, they’re invaluable for post-incident investigations. Analysts can reconstruct an attack step by step, identifying exactly what occurred.
4.4. Customization and Control
Organizations can define their own detection rules, dashboards, and alert logic. This flexibility allows fine-tuning for unique business processes and threats.
However, that same flexibility brings challenges. SIEMs demand ongoing tuning, skilled staff, and continuous updates to stay relevant against evolving threats.
5. The Advantages of MDR
MDR exists because many organizations realized that tools alone don’t stop attackers. They needed expertise and constant attention.
5.1. 24/7 Monitoring
Cyberattacks don’t wait for business hours. MDR providers operate around the clock, ensuring no incident slips through while your staff sleeps.
5.2. Threat Hunting and Intelligence
MDR services combine global threat intelligence with behavioral analytics. Their teams look for subtle indicators of compromise that automated systems might miss.
5.3. Speed of Response
The most significant advantage of MDR is speed. When a real threat is identified, MDR analysts can contain or mitigate it immediately, drastically reducing potential damage.
5.4. Cost-Effective Expertise
Hiring, training, and retaining cybersecurity professionals is expensive. MDR gives organizations instant access to top-tier expertise without building an internal SOC.
5.5. Continuous Improvement
A quality MDR provider learns from each incident — updating detection rules, improving response playbooks, and sharing insights across clients, enhancing everyone’s defense.
6. SIEM and MDR: Better Together
While comparisons often frame SIEM and MDR as competitors, the most mature security programs use both — each covering what the other lacks.
The Complementary Model
- The SIEM acts as the data lake — gathering logs, providing audit trails, and enabling internal compliance reporting.
- The MDR uses this data (or its own sensors) to actively hunt for threats, triage alerts, and execute response actions.
When integrated correctly, SIEM provides the raw intelligence, and MDR transforms it into operational outcomes. Together, they create a complete detection and response ecosystem.
Real-World Example
Imagine an employee’s credentials are stolen:
- The SIEM detects an unusual login from a foreign IP.
- An alert is generated and passed to the MDR team.
- MDR analysts confirm it’s malicious activity.
- They immediately isolate the endpoint, reset credentials, and remove malicious access.
- The SIEM logs the entire event chain for compliance and review.
The partnership between SIEM’s visibility and MDR’s expertise turns a potential breach into a controlled incident.
7. Choosing the Right Fit for Your Organization
7.1. When to Choose SIEM
- You have an established IT or SOC team.
- Compliance and log retention are high priorities.
- You want full control over data and detection rules.
- Your organization can manage 24/7 alert response internally.
7.2. When to Choose MDR
- You lack in-house security expertise or staff.
- You want a turnkey solution with rapid threat response.
- You operate in industries prone to attack (finance, healthcare, manufacturing).
- You need predictable, subscription-based pricing for cybersecurity services.
7.3. When to Use Both
- You’re a mid-to-large organization aiming for complete coverage.
- You already use a SIEM but struggle with alert fatigue.
- You want external experts to manage detection and response while maintaining data ownership internally.
- You value both compliance visibility and rapid incident remediation.
8. Implementation Tips and Best Practices
For SIEM:
- Start with clear goals. Don’t try to ingest every log source at once — focus on the most critical systems.
- Automate routine analysis. Use correlation rules and dashboards to reduce manual workload.
- Tune constantly. Remove noisy rules, update use cases, and refine detection logic regularly.
- Integrate with SOAR tools. Security Orchestration, Automation, and Response platforms can accelerate investigation and remediation.
- Train analysts. The tool is only as good as the people operating it.
For MDR:
- Choose a provider carefully. Look for transparency, SLAs, and clear definitions of “response.”
- Define escalation paths. Know exactly how and when the provider will contact your internal team.
- Integrate with your environment. Ensure the MDR has access to critical systems, endpoints, and logs.
- Review performance metrics. Measure improvements in Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
- Maintain collaboration. Even though MDR is managed, it should operate as an extension of your internal security team.
9. The Future of Threat Management
The lines between SIEM and MDR are starting to blur. As technology advances, we’re seeing converged platforms that combine the data aggregation power of SIEM with the proactive capabilities of MDR. This convergence is accelerating through XDR (Extended Detection and Response) — solutions that integrate endpoint, network, and cloud telemetry into unified analytics.
Emerging Trends
- AI-Driven Detection: Machine learning models are increasingly used to reduce false positives and predict emerging attack patterns.
- Cloud-Native SIEM: Traditional on-prem SIEMs are giving way to scalable, cloud-based platforms that handle massive data volumes with lower overhead.
- Hybrid SOC Models: Organizations are blending internal analysts with external MDR partners for 24/7 coverage and cost optimization.
- Outcome-Based Security: The focus is shifting from tool ownership to measurable outcomes like reduced breach risk, faster recovery, and lower operational burden.
Ultimately, the industry is moving toward integrated, intelligence-driven ecosystems — where visibility, automation, and human expertise merge seamlessly.
10. Common Misconceptions
Even seasoned IT professionals sometimes misunderstand the role of each system. Let’s debunk a few myths.
Myth 1: “MDR Replaces SIEM.”
Not entirely. While MDR includes detection and response, it still benefits from SIEM data. Many MDR providers ingest SIEM logs as part of their visibility layer.
Myth 2: “SIEM Alone Is Enough.”
A SIEM tells you something happened. It doesn’t necessarily stop it. Without trained staff or a managed service, alerts can pile up, leaving incidents unresolved.
Myth 3: “MDR Means Outsourcing Everything.”
MDR is collaborative. You still maintain governance and decision-making authority; the provider handles operational detection and response tasks.
Myth 4: “Only Big Companies Need These Tools.”
Cybercriminals increasingly target small and midsize businesses because they often lack defenses. Both SIEM and MDR can be scaled to fit different budgets and sizes.
11. Measuring Success
No matter which route you choose, the ultimate measure of success lies in outcomes:
- Reduced MTTR: Faster detection and containment of threats.
- Lower Incident Volume: Fewer successful attacks over time.
- Improved Compliance: Consistent log retention and reporting.
- Enhanced Confidence: Stakeholders, clients, and regulators trust your security posture.
Security is no longer about preventing every single intrusion — it’s about resilience. The ability to detect, respond, and recover swiftly defines modern cyber maturity.
12. Conclusion: Visibility Meets Vigilance
So, which one should you choose — SIEM or MDR?
If you want control, visibility, and compliance, start with SIEM.
If you want expertise, response speed, and peace of mind, consider MDR.
If you want both protection and insight, combine them strategically.
Cybersecurity today is not a matter of tools versus services; it’s a matter of visibility plus vigilance. SIEM provides the eyes. MDR provides the reflexes. Together, they form the heartbeat of a resilient security program — one that can see, think, and act before threats can cause real harm.
As attackers become more automated, the organizations that thrive will be those that combine technology, intelligence, and human expertise into a single, cohesive defense system. Whether through SIEM, MDR, or both, the goal remains the same: stay aware, stay adaptive, and stay ahead.