Subscribe to learn about new product features, the latest in technology, solutions, and updates.

Cloud Computing
Why Cloud Workload Protection Matters for Startups Today’s...

cloud security
Cloud storage containers (such as Azure Blob containers,...

Cyber Security
Attack vectors in cybersecurity are the routes, methods,...

cloud security
Cloud security has matured fast—but the terminology hasn’t...

Risk Management
Contemporary organizations function within a landscape characterized by...

cloud security
Cloud computing has transformed how businesses develop, deploy,...

Application Security
Containers have transformed how modern applications are built,...

AI Security
Artificial intelligence (AI) is no longer a concept...

Cyber Security
Cybersecurity is now required in the modern digital...

AI Security
In complex, dispersed environments, visibility, control, and ongoing...

Cyber Security
Organizations are changing the way they think about...

Cloud Computing
Organizations today are no longer satisfied running their...

Cloud Computing
Retail has changed more in the last 10...

Cyber Security
As organizations collect and store more data than...
Application Security
In today’s digital world, security is no longer...

Cloud Computing
Cloud computing changed how we deliver software. We...
Cyber Security
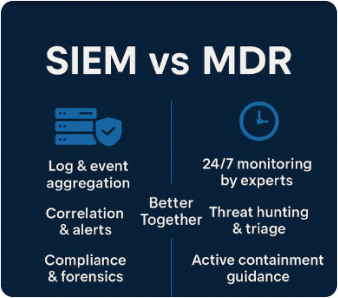
In the ever-evolving world of cybersecurity, businesses face...

Cyber Security
In today’s hyperconnected digital economy, cybersecurity is no...

Cloud Computing
The Hidden Threat of Configuration Drift In modern...

Cyber Security
From Discovery to Decisions The modern enterprise faces...

Risk Management
Whether SLSA is the best standard for CI/CD...

Security Automation
Why prevention still matters (even in 2025) How...

Application Security
In today’s hyperconnected digital ecosystem, applications have become...

Cloud Computing
As organizations evolve, so do threats, tools, and...

AI Security
Kubernetes is now the most common way to...

AI Security
Data is an organization's most valuable asset in...

AI Security
A SOC agent is an AI-powered software worker...

AI Security
Cloud adoption has accelerated over the last decade...

AI Security
Cybersecurity has always been a race between defenders...

AI Security
This piece explores the agentless vs. agent-based argument,...

AI Security
In this expanded guide, we’ll explore what cloud...

AI Security
This guide covers everything from what vulnerability scanning...
Start building today!
Experience the Kosmic Eye difference and unlock the true potential