Cloud security has matured fast—but the terminology hasn’t gotten any simpler. Two acronyms that regularly get mixed up (and sometimes mistakenly used interchangeably) are CASB and CSPM.
They’re related, but they solve different problems:
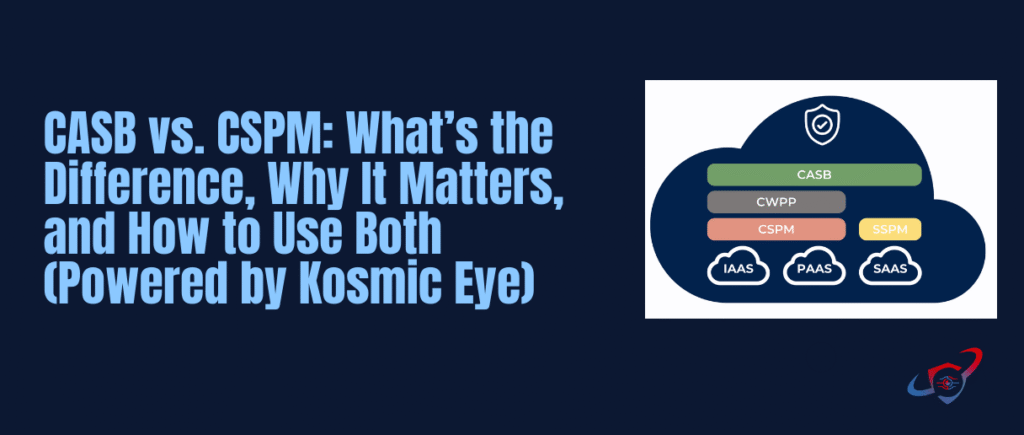
- CASB (Cloud Access Security Broker) focuses on how users access cloud apps and what they do with datainside those apps.
- CSPM (Cloud Security Posture Management) focuses on how your cloud infrastructure is configured and whether it matches security best practices and compliance policies.
If you’re an IT leader, security manager, or cloud owner trying to reduce risk without adding chaos, understanding the difference will help you invest smarter—and build a cleaner operating model.
This guide breaks down CASB vs. CSPM in practical terms, when each is needed, where they overlap, and how a unified approach—powered by Kosmic Eye—helps you prioritize what matters and move faster with confidence.
What is CASB?
A Cloud Access Security Broker is a security control point that sits between your users and the cloud services they access (think: Microsoft 365, Google Workspace, Salesforce, Box, Slack, ServiceNow, etc.).
CASB’s main job: Secure cloud application usage and protect data in SaaS.
Common CASB capabilities
- Visibility into cloud app usage
Identify which apps users are accessing (including “shadow IT”). - Data protection & DLP
Prevent sensitive data from being uploaded, shared publicly, or exfiltrated. - Access control & policy enforcement
Enforce rules like “finance files can’t be shared externally.” - Threat protection
Detect risky behavior such as impossible travel, suspicious downloads, or compromised accounts. - Encryption / tokenization (some CASBs)
Protect data fields in SaaS environments.
CASB example (real-world)
Your employee uploads a spreadsheet containing customer data to a personal cloud drive or shares a private document publicly. A CASB can detect it and apply policy actions—block, quarantine, alert, or enforce encryption.
Think of CASB as: “Security for cloud apps and user behavior.”
What is CSPM?
A Cloud Security Posture Management tool continuously checks cloud environments (AWS, Azure, GCP) for configuration issues, risky settings, and compliance gaps. CSPM’s main job:
Prevent cloud breaches caused by misconfiguration.
Common CSPM capabilities
- Misconfiguration detection
Open storage buckets, publicly exposed databases, permissive IAM policies, insecure network rules. - Policy & compliance checks
Align with frameworks like CIS benchmarks, SOC 2, ISO 27001, NIST, HIPAA. - Continuous monitoring
Configurations change constantly—CSPM keeps watching and reporting drift. - Risk scoring & prioritization (varies by product)
Help teams decide what to fix first. - Infrastructure-as-Code scanning (often included)
Detect issues before deployment via Terraform/CloudFormation scanning.
CSPM example (real-world)
A cloud storage bucket becomes publicly accessible due to a configuration change. CSPM flags the exposure, identifies the resource, and tells you what to remediate.
Think of CSPM as: “Security and compliance for cloud infrastructure configuration.”
CASB vs. CSPM: The Core Differences
Here’s the simplest way to separate them:
- CASB = Protect SaaS usage + data + user actions
- CSPM = Protect IaaS/PaaS configuration + cloud posture
Quick comparison table
| Category | CASB | CSPM |
| Primary focus | SaaS apps and user behavior | Cloud infrastructure configuration |
| Key risk addressed | Data leakage, shadow IT, risky access | Misconfigurations, exposed services, compliance drift |
| Typical environments | Microsoft 365, Salesforce, Google Workspace | AWS, Azure, GCP (accounts/subscriptions/projects) |
| Main stakeholders | IT, Security, Compliance | Cloud team, DevOps, Security, Compliance |
| Common outputs | DLP events, risky app usage, access policy violations | Misconfiguration findings, posture dashboards, compliance reports |
| Best for | Controlling data movement in SaaS | Hardening cloud environments and reducing exposure |
Where CASB and CSPM Overlap (and Why It Gets Confusing)
There is overlap in visibility and policy enforcement, especially as platforms evolve into “all-in-one” suites. You may see vendors bundle features under broader categories like SSE (Security Service Edge) or CNAPP (Cloud-Native Application Protection Platform).
But overlap doesn’t mean redundancy. Overlap areas
- Identity and access signals
Both may surface risky access patterns. - Compliance reporting
CASB helps for SaaS compliance; CSPM helps for cloud infrastructure compliance. - Risk scoring
Both may prioritize issues, but from different angles.
Why confusion happens Organizations say “cloud” and mean different things:
- Some mean SaaS (email, CRM, files)
- Some mean AWS/Azure/GCP infrastructure
- Most mean both
CASB and CSPM exist because cloud risk comes from two separate sources:
- People and data in SaaS
- Infrastructure configuration in IaaS/PaaS
When You Need CASB
CASB is critical when your biggest risks look like:
- Sensitive data is stored or shared in SaaS platforms
- Users connect personal devices or unmanaged networks
- Shadow IT is widespread (employees adopting tools without approval)
- You need stronger governance over who can access what
- You’re dealing with regulated data and must enforce DLP
Strong CASB use cases
- Prevent external oversharing (public links, external sharing mistakes)
- Control downloads from corporate cloud drives
- Detect compromised accounts behaving abnormally
- Reduce shadow IT by cataloging and controlling app usage
- Enforce policies based on user role, device posture, or location
When You Need CSPM
CSPM becomes essential when you run cloud infrastructure and your biggest risks look like:
- Publicly exposed storage, databases, or workloads
- Overly permissive IAM roles and policies
- Network rules that allow inbound from anywhere
- Compliance frameworks require continuous reporting
- Cloud teams ship fast and configuration drift happens daily
Strong CSPM use cases
- Find open S3 buckets / public blob storage
- Identify insecure security groups / firewall rules
- Detect IAM over-permissioning and privilege creep
- Monitor compliance drift over time
- Validate cloud configs against best practices continuously
Do You Need Both?
In many organizations: Yes.
Because most enterprises operate in a hybrid reality:
- SaaS for productivity and business operations
- Cloud infrastructure for applications, APIs, data, and workloads
A practical decision rule
- If you’re worried about data leaving SaaS → CASB
- If you’re worried about cloud resources being exposed → CSPM
- If you’re worried about both (you are) → CASB + CSPM, integrated with a unified prioritization layer
The Real Challenge: Too Many Findings, Not Enough Action
Even with CASB and CSPM deployed, teams often struggle with:
- Hundreds or thousands of alerts/findings
- Conflicting priorities between IT, security, and cloud engineering
- Lack of context (what’s truly critical vs. “best practice”)
- Time lost correlating identity signals, cloud configs, and app activity manually
This is where organizations need an intelligence layer that unifies signals and helps teams focus.
Powered by Kosmic Eye: Turning CASB + CSPM Signals into Prioritized Action
Kosmic Eye is built to help teams move from visibility to decisioning.
Instead of treating CASB and CSPM as separate dashboards, Kosmic Eye helps unify what matters most by:
- Bringing scattered security + infrastructure signals into one view
- Enriching findings with context (assets, identity, environment signals)
- Prioritizing remediation so teams focus on the highest-impact issues first
- Producing workflow-ready outputs that support patching, change control, and remediation
This matters because the biggest operational blocker in cloud security is rarely “lack of tools.”
It’s lack of clarity.
When IT leadership has a consolidated, prioritized view, you get:
- Faster decisions across teams
- Less time spent chasing low-value findings
- More measurable improvements in risk reduction and remediation throughput
How CASB + CSPM Fit into Modern Architectures (SSE, CNAPP, and Beyond)
The cloud security ecosystem keeps expanding. You’ll commonly hear:
- SSE (Security Service Edge): Often includes CASB, SWG, ZTNA, DLP
- CNAPP (Cloud-Native Application Protection Platform): Often includes CSPM plus workload and container security, IaC scanning, etc.
These categories are helpful, but they can also lead to buying overlaps without improving outcomes.
A cleaner way to think about it:
- CASB protects SaaS usage and data
- CSPM protects cloud configuration
- Kosmic Eye helps teams prioritize and operationalize the findings across both
Implementation Tips: Getting Value Without Creating More Noise
If you’re deploying CASB
- Start with visibility + shadow IT discovery
- Define 5–10 high-value data policies (avoid 100+ rules day one)
- Align policies with business workflows (not just security wishes)
- Focus on “external sharing” and “sensitive downloads” early
If you’re deploying CSPM
- Start with the most common high-impact risks:
- Public exposure
- IAM over-permissioning
- Weak network rules
- Assign ownership per cloud account/subscription/project
- Make remediation achievable (ticketing + change control + timelines)
- Track drift over time, not just point-in-time compliance
If you’re doing both
- Don’t run them as isolated islands
- Establish a unified risk triage process across IT, security, and cloud engineering
- Use a central prioritization approach (this is where Kosmic Eye fits naturally)
Choosing the Right Tooling
Ask these questions before buying or expanding:
For CASB
- Which SaaS apps matter most to us?
- Do we need API-based controls, inline controls, or both?
- How strong is DLP and external sharing governance?
- Can it help with shadow IT discovery and control?
For CSPM
- Which clouds do we run (AWS/Azure/GCP)?
- Does it support our compliance requirements?
- How good is IAM and exposure analysis?
- Can it integrate into our DevOps workflows (IaC scanning, ticketing)?
For operational success (the missing piece)
- Can we unify findings and prioritize based on business impact?
- Can we turn outputs into actions (tickets, remediation plans, change control)?
- Can leadership see progress clearly without drowning in dashboards?
Bottom Line
CASB and CSPM are not competitors—they’re complements.
They protect different layers of cloud risk:
- CASB: SaaS usage, data governance, and user behavior
- CSPM: Cloud infrastructure configuration, posture, and compliance drift
The winning strategy is combining both—and avoiding the trap of “more tools = more security.”
A modern approach is:
- Use CASB and CSPM for coverage
- Use an intelligence layer powered by Kosmic Eye to unify signals, add context, and prioritize the highest-impact actions